
Different Types & Causes of a Data Breach
When people think about the causes of a data breach, the first thing to come to mind will almost certainly be hacking. However, not all breaches are a direct result of illegal activities by external sources; some can happen accidentally. Therefore, in order to ensure your cyber security and data protection measures are as robust as possible, it’s important to first understand the different types of breaches that can occur.
Different causes of data breach
External Risks:
- Hacking
- Malware
- Main-in-the-middle (MitM) & eavesdrop attacks
- Phishing
- Business email compromise (BEC)
- Ransomware
- Password guessing
- Keystroke loggers
- Physical theft
Internal risks:
Ransomware
Ransomware has become the most dangerous threat in the world of cyber security with the UK National Cyber Security Service listing it as the most common threat from external actors. It is a type of malicious software that encrypts files and demands payment from the victim to restore access to those files. This form of cyber attack has been around for over a decade, but it has grown more sophisticated with time.
Ransomware can be delivered through various channels, including email attachments, social media messaging, or infected websites. Once it infects a victim's system, it will encrypt their files and display a message demanding payment in exchange for the decryption key. Cyber criminals often use Bitcoin or other cryptocurrencies as they are difficult to trace.
The consequences of ransomware attacks can be devastating, leading to data loss, financial damage and even reputational harm. Victims often face a difficult decision: either pay the ransom or lose access to their valuable data forever. Cyber criminals typically demand payment in cryptocurrency such as Bitcoin, which makes it difficult for authorities to track them down.
Hacking
Hacking looks for weaknesses in a system which can be exploited in order to gain access, and can either be automated or performed manually in a highly targeted campaign.
Once they have gained access, they may have different purposes. In some cases, hackers (also referred to as “threat actors” within the context of cyber security) are after personal data as this can be sold on the “Dark Web”, earning criminals thousands and in some cases, millions of pounds.
Others hack websites or systems to install malicious code for other purposes such as remote monitoring, remote access, or potentially even to market things such as Viagra via hidden links in website code of an unwitting site.
And it’s not just high profile companies who are at risk.
If you have a Wordpress site, it’s highly likely that the site is receiving automated attacks on a daily basis. If you’re surprised (or concerned) by that and would like to check for yourself, install the “Word Fence” plugin. You’ll start to receive alerts for each automated attack. However, don’t panic. Adding Word Fence alone can help improve the security of your site, and the fact that you’ve put in place some measures to increase site security and monitor for any attacks may help you demonstrate you’ve taken reasonable steps to protect data, which could be invaluable in defending against a fine at a later date.
Malware & Viruses
Similar to hacking, malware and viruses can either cause a catastrophic failure resulting in a very clear indication of a breach (e.g. a computer system completely crashes or has all of its data wiped), or could be invisible to the typical user with a goal of sitting quietly on the host system undetected. Often, this type of attack will use the victim’s system to then perform various actions in such a way that if it’s ever discovered, it will be traced back to a victim’s machine, and not that of the hacker.
Malware and viruses are often installed via opening an email with an infected attachment or clicking a link which automatically instals the malicious software onto the victim’s system(s).
Man-in-the-middle & Eavesdrop attacks
This type of attack relies on any vulnerabilities in data protection during transmission between two data sources. This could be as data is sent via an unsecured network, via email, or over VoIP (Voice over IP) telephone calls.
An analogy would be to imagine you’re at a tea point at work chatting with a colleague about something you didn’t want anyone else to hear. However, because you hadn’t considered the risks, you didn’t realise that another colleague was able to overhear your conversation. They could then use what they overheard against you.
MitM attacks work in a similar way, and by ensuring communication between multiple points is always encrypted you can help minimise the risks.
This is why it’s recommended that websites use SSL (Secure Socket Layer) as this can help reduce some of the risks for users.
Phishing
Phishing has significantly increased in recent years and is now one of the biggest risks to data subjects as, unlike hacking, the user often unwittingly and unwillingly compromises their own data. In fact, results from the UK Government’s 2022 Cyber Security Breaches Survey revealed that 39% of surveyed businesses identified a cyber attack in 2021/22, with phishing attempts representing the most common risk vector at 83%.
Phishing is a type of cybercrime where the criminal sends an email or text message, or makes a phone call to the victim, and pretends to be someone else…. such as the victim’s bank, internet provider or even the police!
There are 5 main types of phishing attacks:
- Email Phishing - typically a generic email which looks convincing, but isn’t from the true sender. Here’s an example provided by Royal Mail
- Spear Phishing - A more targeted and convincing type of phishing attack where the criminal may be able to include personal data about the user to build trust
- Whaling - Aimed more at high value targets and senior personnel
- Smishing and Vishing - Text and phone communication is used as the chosen method of attack
- Angler Phishing - A fairly new type of attack which is more prominent for targeting victims on social media
The scammer then asks the victim to provide them with certain sensitive data such as passwords, date of birth, mothers maiden name or credit card details which criminals can then use and sell until such a time as the victim becomes away, or another party such as the victim’s bank, becomes aware and blocks their access.
It sounds like it shouldn’t work… but in reality, the scammers can be extremely convincing, well practised, and also have ways to convince the victim of their legitimacy.
An example of a phishing scam
You receive a phone call from someone claiming to be from your bank. They say something to make you want to engage, such as their systems have detected unusual activity on your account and suspect your account may be compromised. However, in order for them to discuss it in more detail, they need to verify you are the correct person, and therefore need to take you through a few security questions.
At this point, the victim may become suspicious or just be wary and want to protect their data. The scammers have a way to deal with this.
They will often encourage you to hang up, call the number on the back of your card, and for them, and then a member of the team will transfer you back to them to continue the call. The victim duly does this, but what they don’t realise is that the scammer hasn’t hung up.
Most of us don’t check for a dialling tone before calling another number (and on mobiles, we don’t have a dialling tone at all), and so the scammer simply stays on the line and passes it to a colleague.
Once the victim has “called” the other number, scammer number two begins talking as if they’ve answered the call. They then offer to transfer the call. The victim feels they’ve verified the caller is from the bank as, to their mind, they called the number on the back of the card, whereas in reality, the original caller has been on the line all the way through.
Why phishing emails with typo’s aren’t as silly as they look!
As an interesting aside, phishing emails will often contain intentional errors such as typos and grammatical errors!
This is another indication of how clever scammers are as this is actually a rather ingenious “self-filtering” method. People who are less likely to be susceptible will spot these errors fairly quickly and realise it’s a scam, which more often than not simply results in them deleting the email.
This means a greater volume of responses, etc. will be from more vulnerable and susceptible victims. Not only does this improve their efficiency and success rates, it also provides criminals with a type of scoring system which increases the value of the data when sold on the dark web. This in-turn, signals to other criminals which victims are more likely to be easy targets, often resulting in some people falling victim to not just one, but multiple scams.
Sadly, it's often the older generation or vulnerable people who fall victim to phishing scams, but they’re also becoming increasingly common for business attacks, especially via email.
How to report phishing scams
You can do your bit to help combat phishing scams and protect more vulnerable members of society by reporting any phishing scams you encounter to: https://www.ncsc.gov.uk/collection/phishing-scams
As of June 2023, over 21 million scams have been reported via the system.
Business Email Compromise (BEC)
Business Email Compromise is a certain type of phishing attack (specifically known as a “spear phishing attack”). It is a type of cyber attack that has been increasing in frequency and sophistication over the past few years. It occurs when a hacker gains access to an organisation's email system and impersonates a legitimate executive, employee, or vendor to initiate fraudulent transactions or information theft. The goal of the attacker is typically financial gain, but it can also involve stealing sensitive data such as intellectual property, customer information, or confidential documents.
The BEC attack relies heavily on social engineering tactics rather than technical exploits or malware. The attacker carefully researches their target organisation through public sources and phishing emails to identify potential victims and gather intelligence on their operations. They then craft convincing emails that trick the recipient into taking action such as wiring money to a fake supplier account or providing login credentials for company systems.
Password Guessing
Password guessing is one of the most common methods used by hackers to gain unauthorised access to personal or corporate accounts. It is a technique that involves systematically trying different combinations of characters until the correct password is found. Password guessing may seem like a simple and outdated method but it remains an effective way for cyber criminals to breach systems and steal sensitive information.
Social media has also aided this type of an attack as people are willingly disclosing a wealth of personal data; data such as birthdays, names, favourite places, football teams, etc which many people still include as part of their passwords. How are threat actors obtaining this type of data so easily? Well, you’ve probably seen (but hopefully not taken part in!) this type of post:
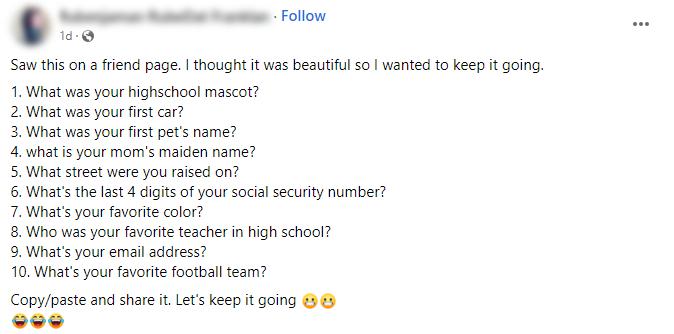
This example is pretty brazen which makes it clear to see how much valuable information you’re giving away. However, others can be far more subtle and may just ask for one or two of the above, but cumulatively over a series of posts, you could still end up giving away far more personal information than you intend to.
In fact, we’ve put together this interesting infographic which shows examples of how many accounts have been breached using a selection of football team names.
We know what you’re thinking; I’ll never fall for that! Well, we imagine many of the people in this Jimmy Kimmel video probably would have said the same. The interesting thing is, if you make people feel comfortable enough, it’s surprising what information people will willingly share!
Password guessing attacks are often carried out through automated tools known as brute force attackers. These programs can generate millions of possible passwords in a short time by using commonly used words, phrases, numbers and symbols. In addition, some hackers use social engineering tactics such as phishing emails or phone calls that trick users into giving away their passwords or sharing personal information that could be used to guess their passwords.
To help combat this type of attack, systems will often limit the number of login attempts allowed within a given timeframe, or will require users to sign up for two-factor authentication which requires a unique code to be sent to the registered users email address or phone number. This code must then be entered as part of the login process; the logic being that even if someone (or an automated script) manages to correctly guess a password, they won’t have access to the legitimate user’s email address or phone.
Keystroke Loggers
A keystroke logger, often called a keylogger, is a type of software or hardware device that monitors and records every keystroke made on a computer or mobile device. Cyber criminals can use these tools to steal personal information such as credit card numbers or login credentials for financial accounts. They can also use them to gain access to confidential company data and trade secrets.
Keystroke loggers can be installed remotely through phishing emails or malware attacks, making them a popular choice for cybercriminals. The danger is compounded by the fact that many keystroke loggers are difficult to detect because they operate in stealth mode, making it possible for hackers to continue collecting data without being caught.
Keystroke loggers are one of the reasons why many financial institutions such as banks switched from using “input” boxes where you could type numbers, to a series of individual drop-down lists of numbers where you need to use a mouse to select the relevant number. However, as safeguards evolve so too do the malicious tools, and sadly many keyword loggers can now also track mouse and trackpad movements.
Physical Theft
When considering digital security, it’s easy to forget about more traditional weaknesses and exploits which could make data vulnerable to theft. Traditional break-ins are still common and some organisations still hold records and sensitive data in paper form in filing cabinets, etc.
In addition, break-ins pose a threat in that digital equipment can either be stolen, cloned, or have malicious software installed such as keyword loggers. Sometimes this can be done so discreetly that the victim is totally unaware that they have been compromised.
However, it’s important to remember that physical theft can also be performed by employees or other visitors who have permission to be on the premises. Their motivation for this can be varied and depending on the nature of the industry, so too can the severity of such a breach.
Physical theft can be reduced by reviewing potential weaknesses of your premises such as replacing single-glazed windows with double glazing and window locks, or ensuring that all ex-employees return any keys or key-fobs upon their departure, or by changing door codes regularly. CCTV is also useful for protecting not only staff and property, but also in being able to go back to identify any potential weaknesses following an intrusion.
Human Error
This is one of the most common causes for an unintentional data breach, and the causes can range from a simple lack of concentration to a need for improved data protection training and awareness.
Between January 2019 and December 2020, nearly 100 devices belonging to parliamentary staffers, including MPs and peers, were lost or stolen. Some of these were due to leaving them in pubs, taxis, cars, and public transport. Others were due to leaving the items unattended. The risk of the latter (eg. if you need to quickly pop away from a table in a cafe to use the toilet) can be reduced by ensuring that devices are securely locked to a fixed object by using a Kensington Lock and ensuring the device is locked so it cannot easily be viewed by a passer-by.
Other examples of human error can include sending emails with sensitive information to an incorrect address or email address, or failing to verify a user’s identity before discussing sensitive information over the phone.
Potential breaches of private data can also happen unintentionally within an office amongst co-workers. For example, someone in a HR department may leave data relating to an employee on a shared printer for longer than necessary, and as a result, another employee (outside of the HR team) may happen to see that data when they go to collect their own print out.
Disgruntled employees or malicious insiders
This relates closely with the physical theft of sensitive data mentioned above and can answer the aspect in regards to motivation. A disgruntled employee may decide to compromise sensitive data in order to gain favour with another entity - whether that be a potential new employer or even at the more severe end, a foreign government.
In some cases journalists have secured employment within an organisation in order to gain information about that organisation. It may be that their intent is ethical (eg. to expose a company which is operating illegally, immorally, etc). However, regardless of the intent, a breach is a breach in the eyes of the ICO and therefore the organisation could be held liable if an unauthorised person gains access to personal data.
Incorrect system or data access permissions
This is another common and easy way to inadvertently weaken the robustness of a system. Many computer systems such as CRMs (Customer Relationship Management software) have a way to manage users and their corresponding permission levels so that the system knows what data they can or can’t access.
If permission levels aren’t set up correctly, or are set too wide, it’s easy to grant users access to data which they should not be able to access or edit. This often happens due to laziness or lack of planning.
It’s not just humans who can be granted the wrong permissions. Many computer systems talk to other internal or external systems, often via means of an API (Application Programming Interface) or TPS (Trusted Proxy Server). This integration with third-party systems, whilst not strictly permissions related, is actually the cause of many data breaches. That’s because, if that external system is compromised, hackers potentially have a direct route into all of the interconnecting systems.
As we write this article, the BBC, British Airways, Boots, payroll provider Zellis and more have fallen victim to a cyber attack of this nature as they use a file transfer system called “MOVEit”.
Therefore, when considering integrating with third-party software, it’s important to:
- consider if you need to introduce a perpetual data integration
- assess whether non-perpetual data exchanges can be facilitated using an alternative approach such as manual data import/exports, or via system connections which only work when enabled, and ensuring they’re disconnected when not in use
- ensure that interlinked systems only have access to the data which they truly need. That way, if a breach via a third party system takes place, the data which is compromised is minimised to the smallest amount possible
Would you know if you’ve suffered a data breach?
Now that you know more about the different types of ways in which data can be breached, the next consideration should be how to identify if you’ve been exposed to a data breach. That’s a topic in its own right so check out our dedicated article: “How to identify and data breach and what needs to happen next”.
Prevention is better than cure - Do you know all of your weak points?
At Databasix, we’re experts in helping organisations improve their data protection and cyber security measures. We understand that no two clients are the same and so we tailor our services to each client to ensure you achieve the best results possible and maximise your ROI. Therefore, if you would like to learn more, please contact us today for a friendly and no-obligation consultation.



